Resolving OpenSSL Heartbleed for VMware ESXi 5.5 Hosts.
| Issue:You need to determine whether or not your VMware ESXi 5.5 Hosts are vulnerable to the OpenSSL Heartbleed vulnerability found in the Open SSL 1.0.1 library. |
| Fix:
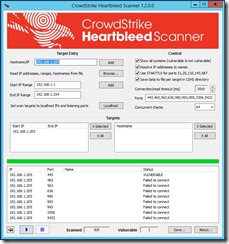
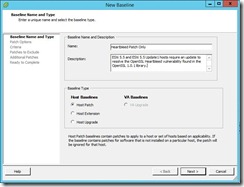
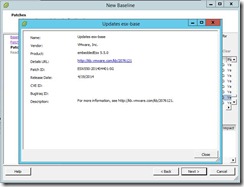
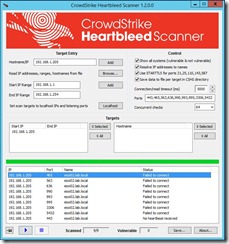
Step # 1 Download the CrowdStrike Heartbleed Scanner. From the URL below. http://www.crowdstrike.com/blog/new-community-tool-crowdstrike-heartbleed-scanner/ Step # 2 After you install CrowdStrike Heartbleed Scanner, you will need to add your VMware ESXi Hosts FQDN or IP Address to the Target Entry List, if you are wanting to only check a single host. I recommend doing this for your first one, so that you get familiar with the tool. Then you can move on to doing a whole list of Hosts or an IP Address Range. In the Target Entry Section, you can either enter a single Host, by FQDN, IP Address or use an IP Address range for multiple Hosts. Step # 3 You will leave all of the default settings on the Control Section, unless you feel that you need to changes any of these settings. Once you have entered your Hosts, you are now ready to start scanning. You can start the Scan using the Blue play button. Next, you can monitor that Scanner, as it is running, it has a circle of dots that stop, when it is done. Once the scan has completed, you will see that results. If a vulnerable Host is found, it will report as “VULNERABLE” in the Status section. Step # 4 Here is how you go about patching your VMware ESXi Hosts. I’m going to be using VMware Update Manager (VUM), to perform my remediation steps. 1) Create a New Baseline, that will include VMware Patch: VMware ESXi 5.5, Bulletin “ESXi550-201404401” a) Add Name b) Add Description c) Baseline Type, I selected Host Baselines, next Host Patch, and then click Next button. d) Patch Options, I selected Fixed, since this New Baseline is for the Heartbleed vulnerability Only. e) Patches, enter ESXi550-201404401, you will need to click on the down arrow and select Patch ID. Next, click on the down arrow to add this patch to your New Baseline, then click the next button. f) You can now click on the Finish button. g) Now, you can attach your New Baseline to your Host. a) Select your Baseline, under Individual Baselines by Type and then click the Attach button. h) Next click on the scan button. Now you should be able to work with VUM as you would normally. 2) Now I will add this VMware Patch to the New HeartBleed Baseline. 3) Here is what a Host will look like if it is not vulnerable to the OpenSSL Heartbleed vulnerability. Under that Status section, it will report as “Failed to connect” Step # 4 You can find more information for your review, on the OpenSSL Heartbleed vulnerability. Resolving OpenSSL Heartbleed for ESXi 5.5 – CVE-2014-0160 (2076665)VMware ESXi 5.5, Patch ESXi550-201404401-SG: Updates esx-base (2076121)http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2076121Response to OpenSSL security issue CVE-2014-0160/CVE-2014-0346 a.k.a: “Heartbleed” (2076225)http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2076225NIST – Vulnerability Summary for CVE-2014-0160https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-0160 |